
Reverse Engineering x64 Basics – Linux on ARM64
As you might already be aware that ARM powers a variety of low-powered devices around us, including but not limited to, phones, routers, IoT devices, […]

As you might already be aware that ARM powers a variety of low-powered devices around us, including but not limited to, phones, routers, IoT devices, […]

Prologue In the previous blog here, we reverse engineered a simple binary containing plaintext password in Linux with the help of GNU Debugger (GDB). In […]

Prologue The main focus of this blog is to give a push start to the beginners to get in the field of reverse engineering. Since […]

Welcome to the part 4 of malware development .In the previous parts 1, 2-1, 2-2 and 3, we created a binary which can listen to […]

In the previous parts 1, 2-1 and 2-2 of this series we created a binary that can connect to, and parse commands sent via netcat […]

In the previous parts of this blog series, I introduced the concept of writing a full-undetectable malware and about writing a client-side socket using […]

Welcome to the second part of the malware development blog series. Here’s the link to Part 1. Given the length of Part 2, I have […]

If you are in cybersecurity, especially Red Teaming, writing a full-undetectable (FUD) malware is a great skill to have. Folks tend to use Metasploit combined […]
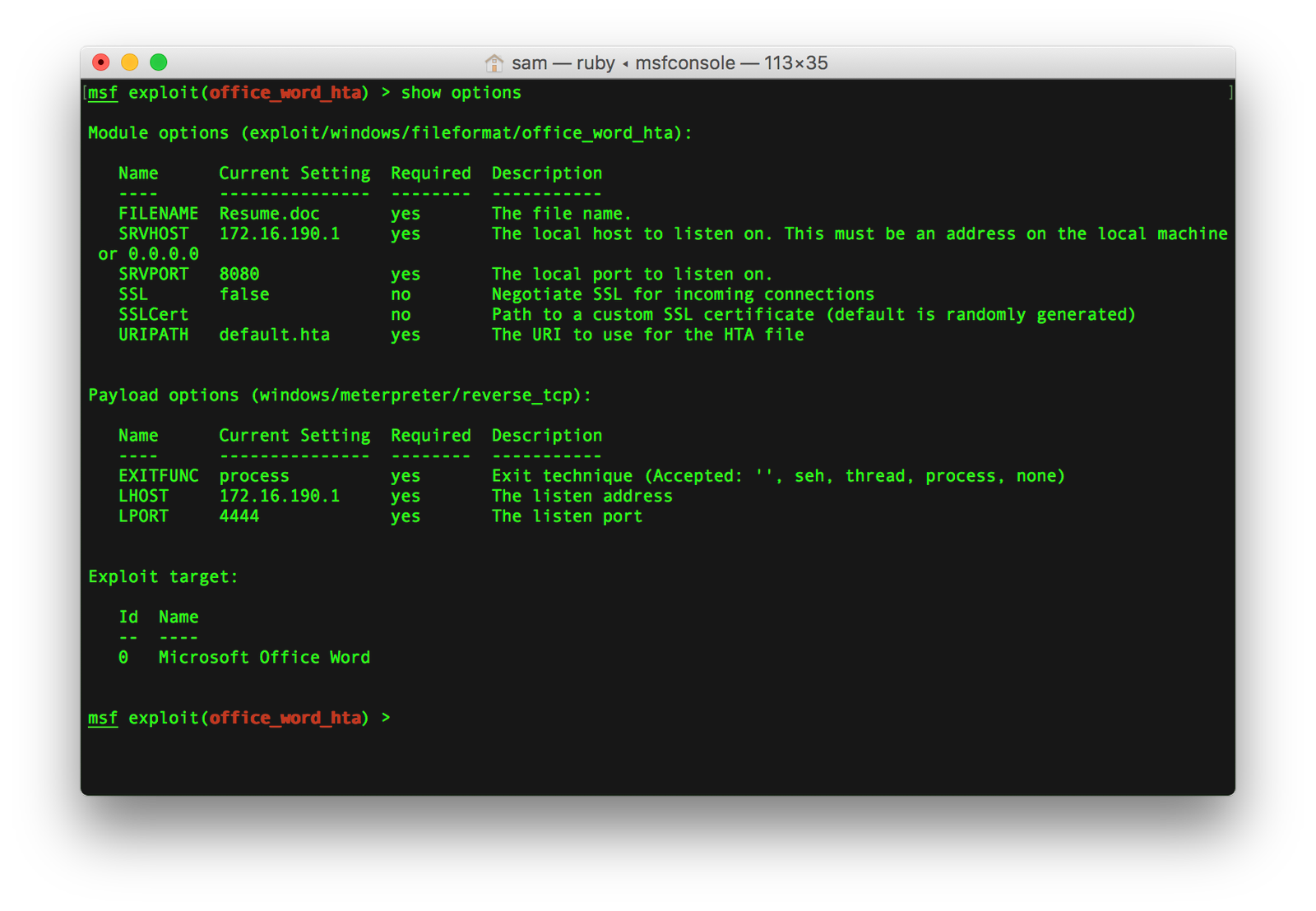
[[Post was originally posted on 23rd May, 2017 at invadersam.com]] Microsoft Office Word / Wordpad remote code execution vulnerability allows a remote attacker to execute […]

Before we start to configure our decoys and put it in our production environment, let’s take a look at what exactly it is and how […]