
Kick-start your Cybersecurity career in 2022
The new year is always a great time to set new resolutions. And a great resolution is to do things that would help on the […]

The new year is always a great time to set new resolutions. And a great resolution is to do things that would help on the […]

Shopping during Christmas is always fun and exciting, but it can get tricky with offers that sound too good to be true. This blog will […]

Did you know that Jingle Bells was the first song played in outer space by the crew of NASA’s Gemini 6A space flight in 1965? Picture, if […]

After the distant social celebrations of 2020, the Christmas season returns to normalcy this year. Families have reunited, shops await the royal bustle, the air […]

An Overview of the most dreaded ransomware in recent times Resurgence of Ransomware In April 2019, the Cybereason Nocturnus team encountered several target machines infected with […]
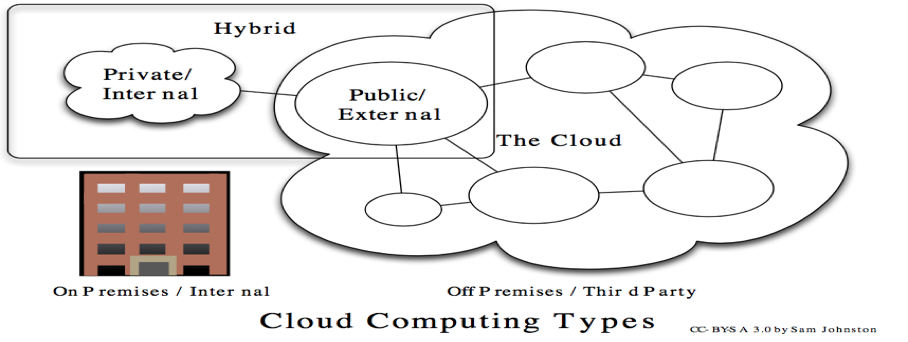
Amazon Web Services (AWS) is a secure cloud platform service which is hybrid of Infrastructure as a Service (IaaS), Platform as a Service(PaaS), and Software […]
Network segmentation plays a vital role while complying with the Payment Card Industry Data Security Standard. Effective segmentation helps in reducing the scope of assessment, […]
Introduction With the onslaught of SMAC – Social Media, Analytics, Mobility and Cloud Computing – in our personal as well as professional lives, we are […]
The Internet of Things and Smart Cities – Security and Privacy Aspects In a world where the technology is constantly improving itself by the hour, […]
Recently, on one of the security mailing lists a query was posted as to what metrics should be produced from a Data Leakage Prevention Solution, an […]